What Type of Device Should You Install as a Decoy to Lure Potential Attackers
In computer terminology, a honeypot is a computer security mechanism set to observe, deflect, or, in some way, counteract attempts at unauthorized use of information systems. Generally, a honeypot consists of information (for example, in a network site) that appears to be a legitimate part of the site and incorporate information or resources of value to attackers. Information technology is actually isolated, monitored, and capable of blocking or analyzing the attackers. This is like to police sting operations, colloquially known as "baiting" a suspect.[ane]
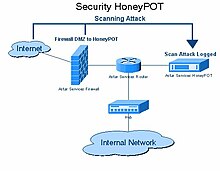
Diagram of an information system honeypot
Types [edit]
Honeypots tin can be classified based on their deployment (utilise/action) and based on their level of interest. Based on deployment, honeypots may exist classified as: [ii]
- production honeypots
- research honeypots
Production honeypots are easy to use, capture simply limited information, and are used primarily by corporations. Production honeypots are placed inside the production network with other production servers by an organization to meliorate their overall country of security. Normally, production honeypots are low-interaction honeypots, which are easier to deploy. They give less information about the attacks or attackers than research honeypots.[2]
Research honeypots are run to assemble information about the motives and tactics of the black hat customs targeting different networks. These honeypots do not add direct value to a specific organization; instead, they are used to research the threats that organizations face and to learn how to better protect against those threats.[iii] Research honeypots are complex to deploy and maintain, capture extensive information, and are used primarily by inquiry, military, or regime organizations.[iv]
Based on design criteria, honeypots can be classified as: [2]
- pure honeypots
- high-interaction honeypots
- depression-interaction honeypots
Pure honeypots are full-fledged production systems. The activities of the aggressor are monitored by using a issues tap that has been installed on the honeypot'southward link to the network. No other software needs to exist installed. Even though a pure honeypot is useful, stealthiness of the defence mechanisms can be ensured by a more controlled machinery.
Loftier-interaction honeypots imitate the activities of the product systems that host a diversity of services and, therefore, an attacker may exist immune a lot of services to waste product their time. By employing virtual machines, multiple honeypots can be hosted on a single concrete machine. Therefore, even if the honeypot is compromised, it can exist restored more than speedily. In general, high-interaction honeypots provide more security by being difficult to detect, but they are expensive to maintain. If virtual machines are non bachelor, one physical calculator must be maintained for each honeypot, which tin can exist exorbitantly expensive. Example: Honeynet.
Depression-interaction honeypots simulate only the services ofttimes requested past attackers. Since they swallow relatively few resources, multiple virtual machines can hands be hosted on one physical system, the virtual systems have a brusque response time, and less code is required, reducing the complexity of the virtual system's security. Example: Honeyd.
Sugarcane is a type of honeypot that masquerades as an open proxy.[v] It tin often take grade as a server designed to wait similar a misconfigured HTTP proxy.[6] Probably the almost famous open proxy was the default configuration of sendmail (before version 8.9.0 in 1998) which would forward email to and from any destination.[7]
Deception technology [edit]
Recently, a new market segment called deception technology has emerged using bones honeypot technology with the addition of advanced automation for calibration. Charade engineering addresses the automatic deployment of honeypot resources over a big commercial enterprise or government institution.[viii]
Malware honeypots [edit]
Malware honeypots are used to detect malware by exploiting the known replication and set on vectors of malware. Replication vectors such as USB flash drives can hands exist verified for show of modifications, either through manual means or utilizing special-purpose honeypots that emulate drives.
Spam versions [edit]
Spammers abuse vulnerable resources such as open up mail relays and open proxies. These are servers which accept e-mail from anyone on the Internet—including spammers—and transport it to its destination. Some organization administrators have created honeypot programs that masquerade as these abusable resource to discover spammer activeness.
There are several capabilities such honeypots provide to these administrators, and the existence of such fake abusable systems makes abuse more difficult or risky. Honeypots can be a powerful countermeasure to abuse from those who rely on very high volume abuse (east.g., spammers).
These honeypots can reveal the abuser's IP address and provide bulk spam capture (which enables operators to decide spammers' URLs and response mechanisms). As described by M. Edwards at ITPRo Today:
Typically, spammers test a postal service server for open relaying past simply sending themselves an email message. If the spammer receives the email message, the mail server plain allows open relaying. Honeypot operators, however, can utilise the relay exam to thwart spammers. The honeypot catches the relay test email bulletin, returns the test electronic mail bulletin, and afterward blocks all other email messages from that spammer. Spammers proceed to apply the antispam honeypot for spamming, only the spam is never delivered. Meanwhile, the honeypot operator tin notify spammers' ISPs and take their Cyberspace accounts canceled. If honeypot operators detect spammers who use open up-proxy servers, they can besides notify the proxy server operator to lock downwardly the server to preclude further misuse.[9]
The apparent source may be another driveling system. Spammers and other abusers may use a chain of such abused systems to make detection of the original starting point of the corruption traffic difficult.
This in itself is indicative of the power of honeypots as anti-spam tools. In the early days of anti-spam honeypots, spammers, with little business organization for hiding their location, felt prophylactic testing for vulnerabilities and sending spam directly from their own systems. Honeypots fabricated the abuse riskier and more difficult.
Spam still flows through open relays, but the book is much smaller than in 2001-02. While virtually spam originates in the U.S.,[10] spammers hop through open relays across political boundaries to mask their origin. Honeypot operators may use intercepted relay tests to recognize and thwart attempts to relay spam through their honeypots. "Thwart" may mean "accept the relay spam but decline to deliver it." Honeypot operators may discover other details concerning the spam and the spammer past examining the captured spam messages.
Open relay honeypots include Jackpot, written in Coffee by Jack Cleaver; smtpot.py, written in Python by Karl A. Krueger;[11] and spamhole, written in C.[12] The Bubblegum Proxypot is an open source honeypot (or "proxypot").[13]
Electronic mail trap [edit]
An email address that is not used for whatever other purpose than to receive spam can also be considered a spam honeypot. Compared with the term "spamtrap", the term "honeypot" might be more than suitable for systems and techniques that are used to discover or counterattack probes. With a spamtrap, spam arrives at its destination "legitimately"—exactly every bit non-spam email would go far.
An constructing of these techniques is Project Honey Pot, a distributed, open source projection that uses honeypot pages installed on websites around the earth. These honeypot pages disseminate uniquely tagged spamtrap e-mail addresses and spammers can then exist tracked—the corresponding spam mail is after sent to these spamtrap due east-mail addresses.
Database honeypot [edit]
Databases ofttimes get attacked past intruders using SQL injection. Equally such activities are not recognized by basic firewalls, companies frequently use database firewalls for protection. Some of the available SQL database firewalls provide/support honeypot architectures so that the intruder runs against a trap database while the web awarding remains functional.[fourteen]
Honeypot Detection [edit]
Merely every bit honeypots are weapons against spammers, honeypot detection systems are spammer-employed counter-weapons. Equally detection systems would likely use unique characteristics of specific honeypots to identify them, such equally the property-value pairs of default honeypot configuration,[15] many honeypots in-employ utilise a set up of unique characteristics larger and more daunting to those seeking to detect and thereby identify them. This is an unusual circumstance in software; a situation in which "versionitis" (a large number of versions of the same software, all differing slightly from each other) tin be beneficial. At that place's also an advantage in having some easy-to-detect honeypots deployed. Fred Cohen, the inventor of the Deception Toolkit, argues that every system running his honeypot should have a charade port which adversaries tin use to detect the honeypot.[sixteen] Cohen believes that this might deter adversaries.
Risks [edit]
The goal of honeypots is to attract and appoint attackers for a sufficiently long menstruum to obtain high-level Indicators of Compromise (IoC) such equally attack tools and Tactics, Techniques, and Procedures (TTPs). Thus, a honeypot needs to emulate essential services in the production network and grant the attacker the freedom to perform adversarial activities to increase its attractiveness to the attacker. Although the honeypot is a controlled environment and can be monitored by using tools such every bit honeywall,[17] attackers may still exist able to use some honeypots as pin nodes to penetrate production systems.[18] This tradeoff between the honeypot attractiveness and the penetration risk has been investigated both qualitatively[19] and quantitatively.[20]
The 2nd risk of honeypots is that they may attract legitimate users due to a lack of communication in large-scale enterprise networks. For example, the security squad who applies and monitors the honeypot may not disclose the honeypot location to all users in fourth dimension due to the lack of communication or the prevention of insider threats.[21] [22] A game-theoretical model[23] has been proposed to simultaneously incentivize adversarial users and disincentivize legitimate users for the honeypot access by exploiting the utility deviation between two types of users.
Dearest nets [edit]
"A 'honey cyberspace' is a network of high interaction honeypots that simulates a product network and configured such that all activeness is monitored, recorded and in a degree, discreetly regulated."
-Lance Spitzner,
Honeynet Project
Ii or more honeypots on a network grade a dear cyberspace. Typically, a honey net is used for monitoring a larger and/or more diverse network in which one honeypot may not be sufficient. Honey nets and honeypots are usually implemented as parts of larger network intrusion detection systems. A honey farm is a centralized collection of honeypots and analysis tools.[24]
The concept of the honey net outset began in 1999 when Lance Spitzner, founder of the Honeynet Project, published the paper "To Build a Honeypot".[25]
History [edit]
The earliest honeypot techniques are described in Clifford Stoll's 1989 book The Cuckoo'due south Egg.
One of the earliest documented cases of the cybersecurity use of a honeypot began in January 1991. On January vii, 1991 while he worked at AT&T Bell Laboratories Cheswick observed a criminal hacker, known as a cracker, attempting to obtain a copy of a countersign file. Cheswick wrote that he and colleagues synthetic a "chroot "Jail" (or "roach motel")" which allowed them to observe their attacker over a menses of several months. [26]
In 2017, Dutch constabulary used honeypot techniques to track down users of the darknet market Hansa.
The metaphor of a bear existence attracted to and stealing honey is mutual in many traditions, including Germanic, Celtic, and Slavic. A common Slavic discussion for the acquit is medved "beloved eater". The tradition of bears stealing beloved has been passed down through stories and sociology, especially the well known Winnie the Pooh.[27] [28]
See too [edit]
- Canary trap
- Customer honeypot
- Cowrie
- Defense strategy (calculating)
- HoneyMonkey
- Honeytoken
- Network telescope
- Performance Trust
- Tarpit
References and notes [edit]
- ^ Cole, Eric; Northcutt, Stephen. "Honeypots: A Security Manager'south Guide to Honeypots".
- ^ a b c Mokube, Iyatiti; Adams, Michele (March 2007). "Honeypots: concepts, approaches, and challenges". Proceedings of the 45th Annual Southeast Regional Briefing: 321–326. doi:10.1145/1233341.1233399. S2CID 15382890.
- ^ Lance Spitzner (2002). Honeypots tracking hackers. Addison-Wesley. pp. 68–lxx. ISBN0-321-10895-vii.
- ^ Katakoglu, Onur (2017-04-03). "Attacks Landscape in the Nighttime Side of the Web" (PDF). acm.org . Retrieved 2017-08-09 .
- ^ Talukder, Asoke Grand.; Chaitanya, Manish (17 Dec 2008). Architecting Secure Software Systems Page 25 – CRC Press, Taylor & Francis Grouping. ISBN9781420087857.
- ^ "Exposing the Underground: Adventues of an Open up Proxy Server". 21 March 2011.
- ^ "Capturing spider web attacks with open proxy honeypots". 3 July 2007.
- ^ "Deception related applied science – its not simply a "prissy to have", its a new strategy of defense – Lawrence Pingree". 28 September 2016.
- ^ Edwards, One thousand. "Antispam Honeypots Requite Spammers Headaches". Windows IT Pro. Archived from the original on 1 July 2017. Retrieved xi March 2015.
- ^ "Sophos reveals latest spam relaying countries". Assist Internet Security. Help Net Security. 24 July 2006. Retrieved 14 June 2013.
- ^ "Honeypot Software, Honeypot Products, Deception Software". Intrusion Detection, Honeypots and Incident Handling Resources. Honeypots.cyberspace. 2013. Archived from the original on eight Oct 2003. Retrieved fourteen June 2013.
- ^ dustintrammell (27 February 2013). "spamhole – The Fake Open SMTP Relay Beta". SourceForge. Dice Holdings, Inc. Retrieved 14 June 2013.
- ^ Ec-Council (5 July 2009). Certified Upstanding Hacker: Securing Network Infrastructure in Certified Ethical Hacking. Cengage Learning. pp. 3–. ISBN978-1-4354-8365-1 . Retrieved 14 June 2013.
- ^ "Secure Your Database Using Honeypot Architecture". dbcoretech.com. August 13, 2010. Archived from the original on March viii, 2012.
- ^ Cabral, Warren; Valli, Craig; Sikos, Leslie; Wakeling, Samuel (2019). "Review and Assay of Cowrie Artefacts and Their Potential to be Used Deceptively". Proceedings of the 2019 International Conference on Computational Science and Computational Intelligence. IEEE. pp. 166–171. doi:10.1109/CSCI49370.2019.00035.
- ^ "Deception Toolkit". All.cyberspace. All.net. 2013. Retrieved 14 June 2013.
- ^ "Honeywall CDROM – The Honeynet Project". Retrieved 2020-08-07 .
- ^ Spitzner, Lance (2002). Honeypots Tracking Hackers. Addison-Wesley Professional person. OCLC 1153022947.
- ^ Pouget, Fabien; Dacier, Marc; Debar, Hervé (2003-09-14). White paper: honeypot, honeynet, honeytoken: terminological issues. EURECOM. OCLC 902971559.
- ^ Huang, Linan; Zhu, Quanyan (2019), "Adaptive Honeypot Engagement Through Reinforcement Learning of Semi-Markov Decision Processes", Lecture Notes in Estimator Science, Cham: Springer International Publishing, pp. 196–216, arXiv:1906.12182, doi:10.1007/978-three-030-32430-8_13, ISBN978-3-030-32429-2, S2CID 195750533
- ^ Qassrawi, Mahmoud T.; Hongli Zhang (May 2010). "Client honeypots: Approaches and challenges". quaternary International Conference on New Trends in Informatics and Service Science: 19–25.
- ^ "illusive networks: Why Honeypots are Stuck in the Past | NEA | New Enterprise Associates". www.nea.com . Retrieved 2020-08-07 .
- ^ L. Huang and Q. Zhu, "Duplicity Games for Charade Design with an Awarding to Insider Threat Mitigation," in IEEE Transactions on Information Forensics and Security, doi:ten.1109/TIFS.2021.3118886.
- ^ "cisco router Customer support". Clarkconnect.com. Archived from the original on 2017-01-16. Retrieved 2015-07-31 .
- ^ "Know Your Enemy: GenII Love Nets Easier to deploy, harder to detect, safer to maintain". Honeynet Projection. Honeynet Project. 12 May 2005. Archived from the original on 25 January 2009. Retrieved 14 June 2013.
- ^ "An Evening with BerferdIn Which a Cracker is Lured, Endured, and Studied" (PDF). cheswick.com . Retrieved 3 Feb 2021.
- ^ "The word for "comport"". Pitt.edu . Retrieved 12 Sep 2014.
- ^ Shepard, E. H., Milne, A. A. (1994). The Complete Tales of Winnie-the-Pooh. Great britain: Dutton Children'south Books.
Further reading [edit]
- Lance Spitzner (2002). Honeypots tracking hackers. Addison-Wesley. ISBN0-321-10895-7.
- Sean Bodmer; Max Kilger; Gregory Carpenter; Jade Jones (2012). Opposite Deception: Organized Cyber Threat Counter-Exploitation. McGraw-Colina Education. ISBN978-0-07-177249-5.
External links [edit]
- The Ultimate Fake Admission Betoken - AP less articulate-text WPA2 passphrase hacking
- Distributed Open Proxy Honeypots Project: WASC
- SANS Institute: What is a Honey Pot?
- SANS Establish: Primal Honeypotting
- Project Honeypot
- A curated listing of honeypots, tools and components focused on open source projects
Source: https://en.wikipedia.org/wiki/Honeypot_%28computing%29
0 Response to "What Type of Device Should You Install as a Decoy to Lure Potential Attackers"
Post a Comment